Finding ADIDNS Unsecure Dynamic Updates setting
13 Dec 2024What is Unsecure Dynamic Updates setting and why it’s interesting for security people
Active Directory depends on its DNS system to discover and communicate with its services. DNS records in AD are stored directly as AD objects with their own full LDAP distinguished name. DNS system in AD support zones so that you can have different configuration for each set of DNS records. DNS zones for an AD forest with a single AD domain wag.local can look like this:
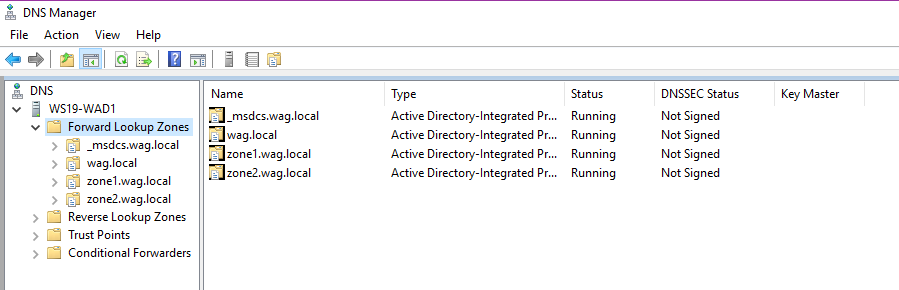
This means there are are 4 zones and each with potentially different configuration. We have _msdcs.wag.local and wag.local which are default and the 2 others created by me. In this article we’re interested in their Dynamic Updates setting.
Dynamic Update setting allows 3 options (see here). As the name of one of them - ZONE_UPDATE_UNSECURE - suggests, this is the unsecure option as it allows anyone to update DNS records fot that zone. By anyone I mean authenticated or not.
This is dangerous settings as it can allow an attacker who can reach AD domain to easily perform man-in-the-middle (MitM) attacks. This was already heavily discussed elsewhere with some references below. The gist is that an attacker could change existing DNS record and thus make other computers and users authenticate to machine they control introducing MitM. This could then be exploited e.g. for authentication relay.
Some references to articles discussing unauthorized ADIDNS access abuse:
- Beyond LLMNR/NBNS Spoofing – Exploiting Active Directory-Integrated DNS
- Spoofing DNS Records by Abusing DHCP DNS Dynamic Updates
- Exploiting stale ADIDNS entries
How to find out Dynamic Updates setting the usual way
If you’re DNS admin you can easily validate this from GUI via dnsmgmt.msc console (install via Remote Server Administration Tools server feature). Alternative may be calling dnscmd.exe /ZoneInfo <zone name> - value 1 of field update should indicate unsecure updates in tool’s output. However, if you’re not DNS admin your GUI and CLI will fail.
How to find out Dynamic Updates as commoner
In case even you’re lowly security engineer without high privileges or a pentester who landed in new network, you may still want to enumerate this information with standard AD account. You try the GUI.
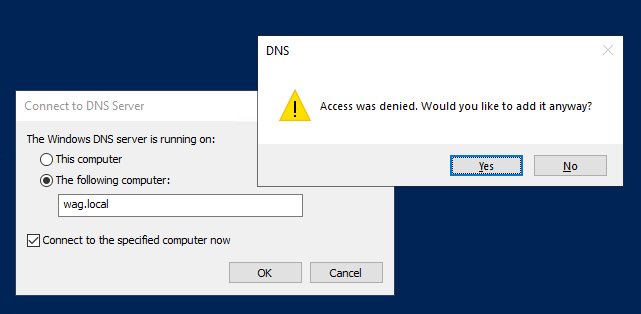
No-go. You try with CLI.
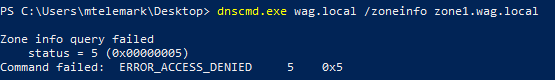
Nope again. Luckily, zone information are stored in Active Directory and it’s possible to query it via LDAP under CN=MicrosoftDNS,DC=DomainDnsZones,DC=<your domain>. As is usual in AD, those who can login shall read everything via LDAP (in this case possibly even Guest accounts). You can see default permissions on zone AD object below.
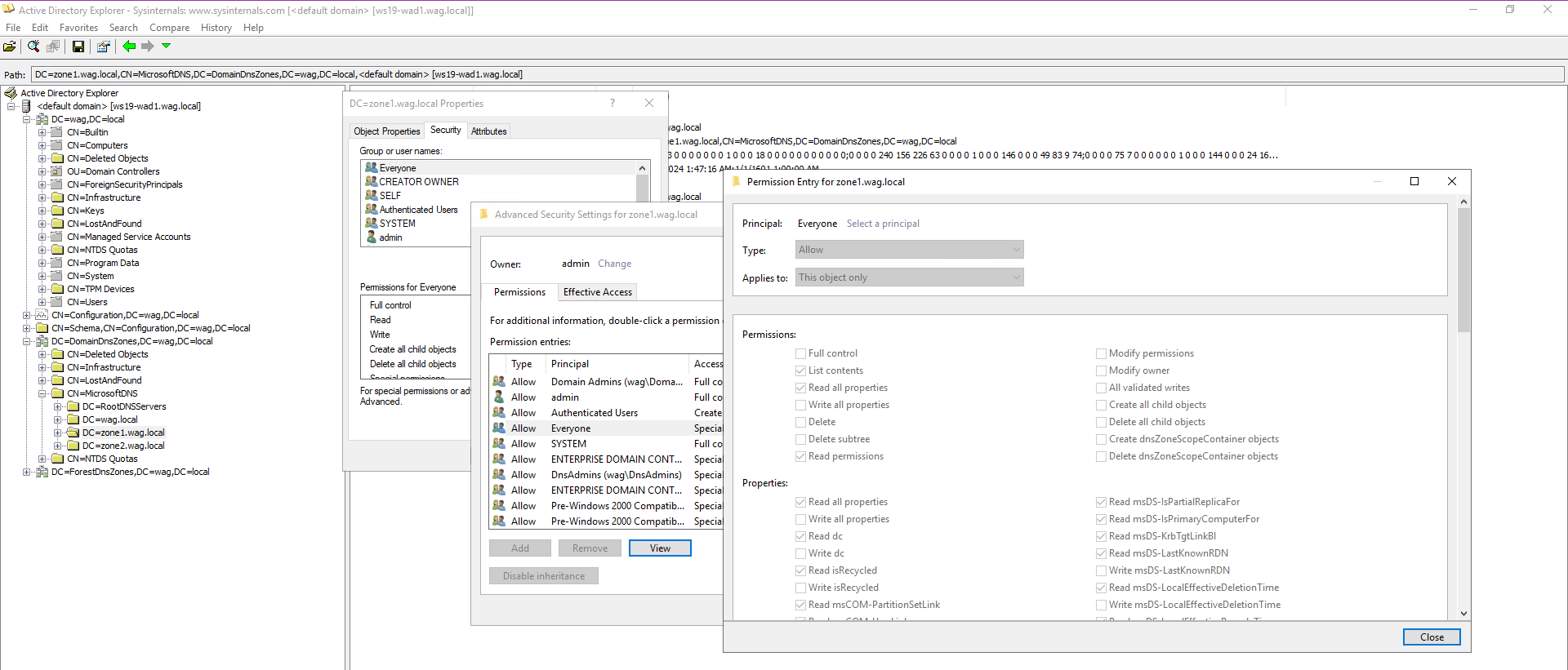
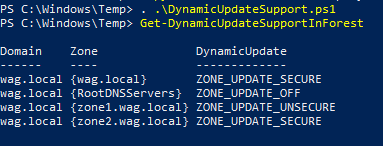
Finally, the meat of this post. Here’s a tool you can use to query this data from PowerShell as any AD user - DynamicUpdateSupport.ps1
This is how output looks like for my test domain.
If I’m wrong about anything or just want to discuss, I’m here: Bluesky & X