Active Directory, whoami?
08 Feb 2022Sometimes it happens that I authenticate as multiple users from either single PowerShell session or in multiple windows. And sometimes I’m not careful and lose track of who is logged-in in where. Using klist does not always show any tickets (because NTLM is used? have yet to find out). In those cases, running traditional whoami.exe may not return correct username if I’ve injected tickets or used runas. It would just be the best to run whoami against Active Directory somehow…
New to me, this is what bugch3ck is doing in his C# project SharpLdapWhoami by using LDAP’s “Who am I?” operation with OID 1.3.6.1.4.1.4203.1.11.3. If you have RSAT with Active Directory Domain Services installed or just System.DirectoryServices.Protocols.dll laying around, you can issue this LDAP whoami also using plain PowerShell like this:
# before running, .NET types from System.DirectoryServices.Protocols.dll need to be loaded, e.g. by Add-Type -Path .\some\path\System.DirectoryServices.Protocols.dll
# or if you have RSAT installed easiest is to auto-import it by running any RSAT command, e.g. "Get-ADUser -?"
$dc = "here goes Domain Controller's hostname or FQDN"
$c = new-object System.DirectoryServices.Protocols.LdapConnection($dc)
$rq = new-object System.DirectoryServices.Protocols.ExtendedRequest('1.3.6.1.4.1.4203.1.11.3')
write-host ([System.Text.Encoding]::ASCII.GetString($c.SendRequest($rq).ResponseValue))
Lastly, an example where I see this super helpful. I see nothing in klist output and whoami.exe doesn’t help. Since I know there should be authenticated session to AD, I connect to domain controller dc01 and do the LDAP whoami:
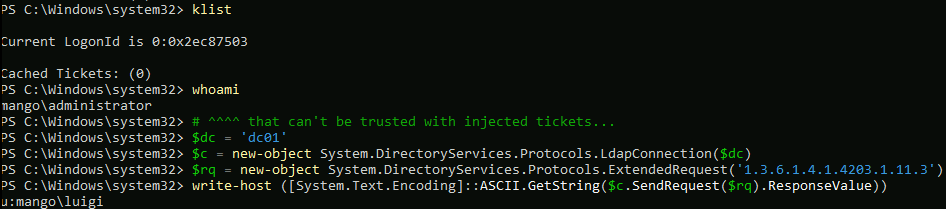
From the output now I know I’m actually authenticated as user luigi to domain mango.